About Brighte
Brighte Capital is a rapidly growing Australian FinTech founded in 2015, making solar, battery, and home improvements affordable for Aussies all over the country.
Its mission is to make every home sustainable, offering Aussie families affordable access to sustainable energy solutions through an easy payment platform.
The company offers financing and zero-interest payment solutions for the installation of solar panels, batteries, air conditioning, and lighting equipment.
The process is simple and fast, all managed via Brighte’s website or smartphone app. Once your application is approved, you get access to highly vetted vendors offering interest-free products. Brighte recently received the Finder Green Awards 2021 in the category of Green Lender of the Year, an incredible achievement that recognises and solidifies its position in the Australian market.
As a company operating in both the Energy Industry and Financial Services Industry, Brighte must comply with numerous standards, rules, and regulations highlighting operations, security, and data protection as key topics. Australian Privacy Principles, Anti-Money Laundering and Counter-Terrorism Financing Act 2006, and National Consumer Credit Protection Act 2009 are just some examples.
But as a customer-centric company, Brighte goes beyond mere compliance requirements. Transparency and making life easier are two of its most important values, so Brighte is alert to other factors which can bring damage to their clients, well beyond compulsory minimum standards.
The Business Challenge: consolidate and improve the core digital platform architecture while prioritising security
Brighte’s business model is impressive and there has been considerable investment in a robust digital platform to support the different areas of the company. There is substantial technology in-place behind the scenes, with the business headed by a dedicated team of professionals with diverse backgrounds and skills, all contributing to a strong work culture.
As a relatively young company, Brighte has experienced exponential growth. Even with best practices in-place, it was difficult to continually manage or upgrade the various IT solutions the business was using.
Most of Brighte’s applications were developed in-house and based on a range of different programming languages and technologies. While its infrastructure was hosted on AWS, different services were being used to support each application, causing issues around ease of management and knowledge retention and sharing, but on top of that, increased vulnerability and manual interactions should have been fixed, retaining and improving security.
Brighte needed to revamp its landscape and reevaluate the current architecture of its core digital platform. The business reached out to DNX, seeking a solution that would improve its cloud strategy, apply DevOps best practices, reduce infrastructure operational overheads, and achieve overall cost optimisation. However, because of its financial conditions, these challenges need to go hand-in-hand with security. Therefore, DNX understood that the challenge is to provide those improvements while prioritising security.
The DNX Solution: infrastructure, pipelines, AWS Stack, deliverables, project, UI, frontend + backend
Prior to project kick-off, DNX began a discovery phase to maximise the information collected about the challenges faced by Brighte’s team. A Well-Architected Review Framework was delivered to identify risks and opportunities against operational excellence, security, reliability, performance efficiency, and cost optimisation pillars. This enabled DNX to ensure and maintain focus on the most important priorities, such as security and operational excellence, while the team went through the DevOps Transformation guidelines to draft a plan for the required changes, working towards continuous innovation during the course of the project.
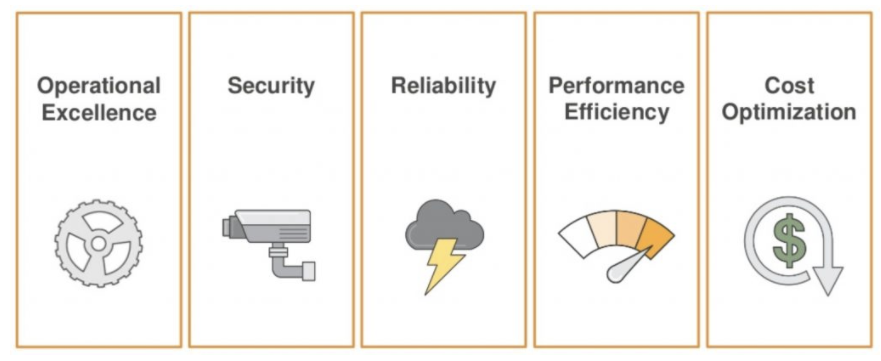
Comparing best practices enables the team to identify new opportunities and highlight concerns that may not be apparent at the beginning.
From an infrastructure perspective, DNX recognised that Brighte needed to improve control over its AWS resources using IaC (Infrastructure as Code) and restructure its AWS organisation and accounts strategy.
To achieve this, DNX suggested its DNX.One Well-Architected Foundation (aka DNX.One) to provide the following benefits:
- New structure of AWS organisation following the best practices in the market.
- Ability to manage all infrastructure resources across all of their AWS accounts based on Terraform and CI/CD pipelines.
- Designed for AWS with Well-Architected principles
It is important to mention that DNX.One is a ready-to-go solution that aims to solve the most common business needs regarding cloud infrastructure, fitting different application architectures (including containers), has flexibility and automation for distinct platforms, and enhances management to keep business under control.
An extra layer of high-level security best practices as default for architecture guarantees continuous security at any stage. It ensures that regardless of the challenges that customers need to achieve, they will do it in a secure way.
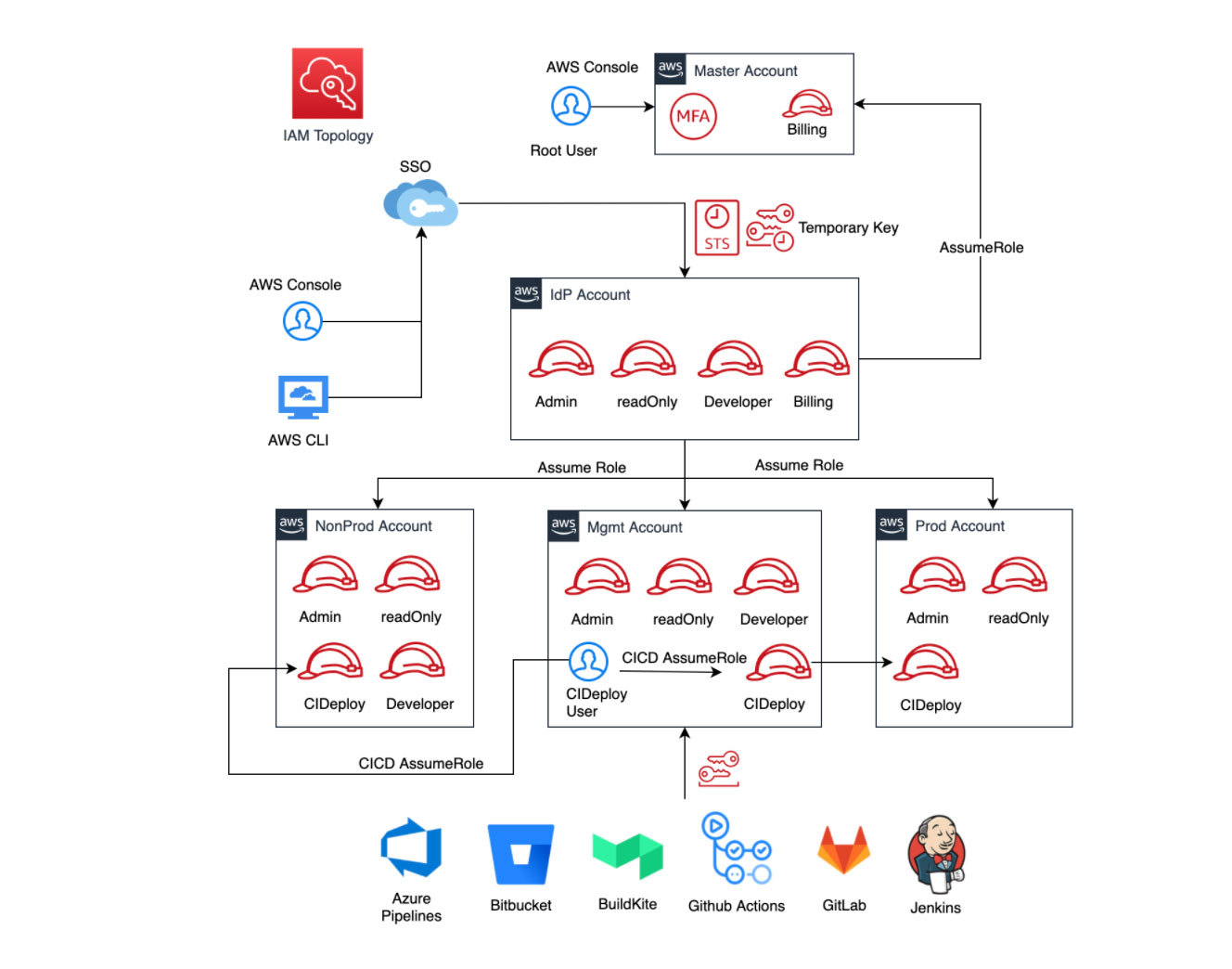
From the applications point of view, DNX identified Brighte was using different types of AWS services to deploy their applications, including ElasticBeanstalk, ECS with Fargate, and EC2 instances.
Having these different types of application deployments is expensive, as the company needs to utilise multiple operational processes to manage the environment, but is also less secure because no single consistent security module is provided, effectively introducing risk.
With its Application Modernisation strategy, DNX suggested containerisation of the client’s main applications and deployment via ECS with spot instances. This change would substantially reduce Brighte’s costs, create a pattern for new applications that may be necessitated by future business growth, and improve security while having a single security pathway to improve the AWS responsibility under the Shared Responsibility Model, making security simpler by using ECS.
The CI/CD pipeline strategy was also evaluated and Brighte’s team demonstrated a willingness to adopt solutions that would reduce the complexity of managing new deployments and providing faster response times to deploy new applications in their landscape.
Key Project Phases:
Cloud Foundation (aka AWS Foundation)
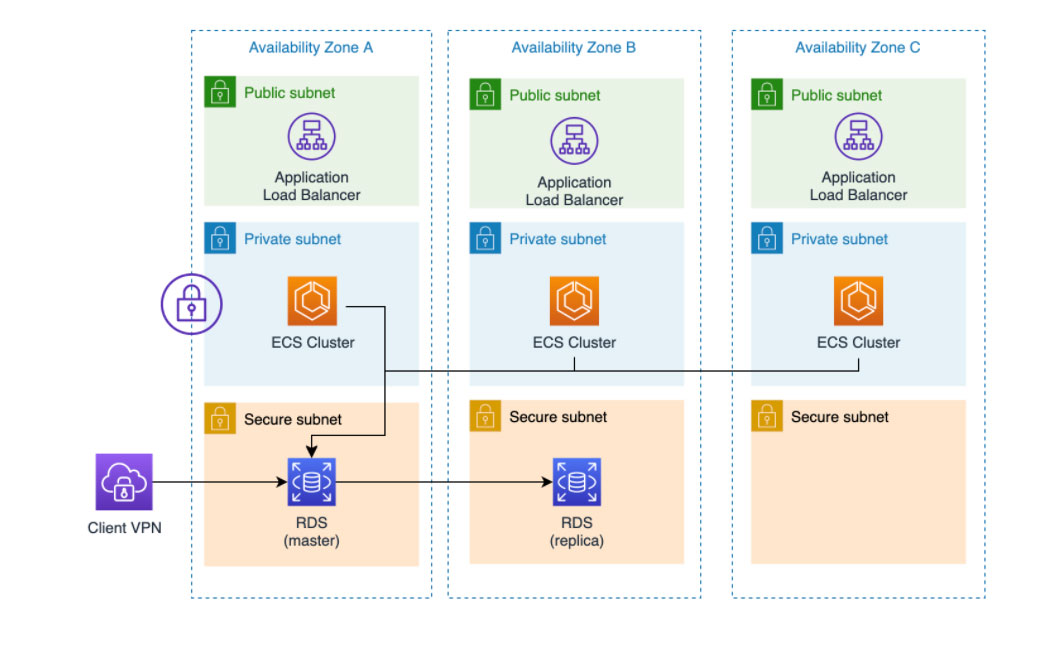
With our automated solutions based on Terraform (IaC), DNX restructured Brighte’s AWS resources such as AWS organisation, accounts, network, domains, VPN, and all the security controls for account access via SSO using Azure AD as their Identity Provider.
Building a strong and secure foundation for Brighte’s applications was a critical first step prior to modernisation. With a multi-AZ strategy with ECS nodes running on spot instances deployed in their environments, Brighte was able to run a cluster of Docker containers across availability zones and EC2 instances, while optimising costs and simplifying the security operating model.
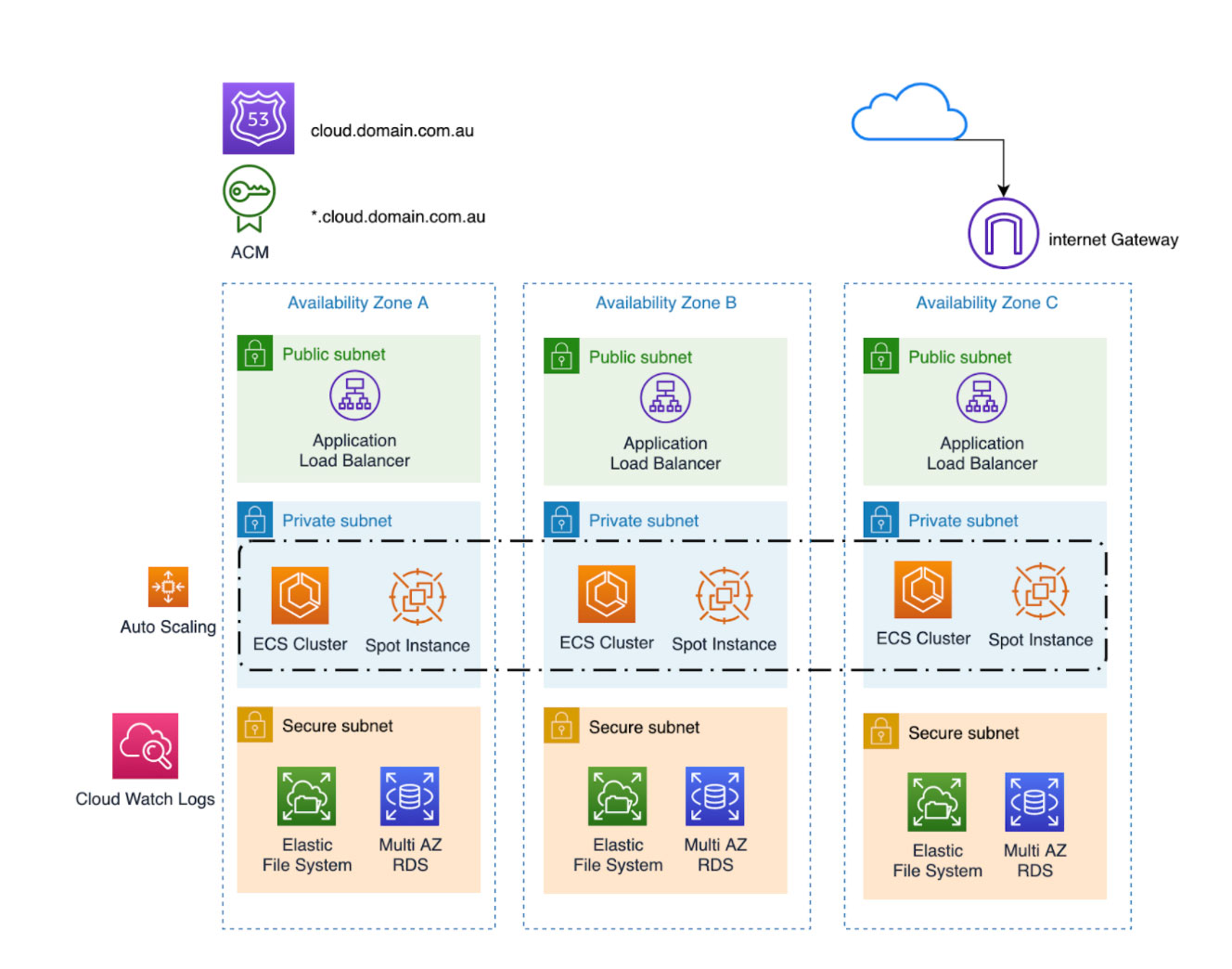
Security:
Although security is considered and addressed at many stages by now, and several cloud technologies have been put in-place to protect data, systems, and assets in a manner to improve security through best-practice guidance, there are some AWS services that still need to be highlighted.
AWS Cloudwatch
The logs from all systems, applications, and AWS services have been centralised in the highly scalable AWS CloudWatch service. It allows easy visualisation and filtering based on specific fields, or archiving them securely for future analysis. CloudWatch Logs enables you to see all of your logs, regardless of their source, as a single and consistent flow of events ordered by time, and you can query and sort them based on other dimensions, group them by specific fields, create custom computations with a powerful query language, and visualise log data in dashboards.
AWS Cloudtrail
All AWS events are reported to a centralised CloudTrail and exported to an S3 bucket in an Audit account.
AWS Organisations
The setup of new accounts has been automated by service control policies (SCPs) which apply permission guardrails at the organisation.
AWS Guardduty:
DNX implemented a centralised Guardduty to detect unexpected behaviour in API calls. The Amazon GuardDuty alerts when unexpected and potentially unauthorized or malicious activity occurs within the AWS accounts.
DNX has helped Brighte to strengthen its workload security along with a number of other relevant AWS resources, such as Amazon Cloudfront, ECR image scanners, AWS IAM identity provider, VPC endpoints, Amazon WAF, and AWS Systems Manager Parameter Store.
Cost savings:
There were three main cost optimisation drivers used for this project. The combined use of these three strategies brought savings in the order of 60%, compared with the same workloads on the previous environment, while allowing Brighte to use several new resources delivering more value with less cost to its clients.
- Using ECS clusters with EC2 Spot Instances: Spot instances are unused AWS capacity that is available for a fraction of the normal On-Demand prices on a bidding model. Spot instances can be reclaimed by AWS when there is no available capacity, so DNX uses an auto-scaling model with several instance types that ensure availability while saving around 75% compared with On-Demand. For instance, an On-Demand t3.xlarge instance costs $0.2112 per hour while the same Spot instance costs $0.0634.
- Savings plans for Databases: As the databases are stable and their use can be predicted over a long duration, AWS allows us to reserve a DB instance for one, two, or three years, with monthly or upfront payments, charging a discounted hourly rate saving from 30% to 60%, according to the chosen plan.
- Automatic scheduler for turning on and off resources according to a usage calendar: For Development and Testing environments, which are not meant to be used on a 24/7 basis, Brighte can easily schedule when these environments are available for the teams and when it should be turned off (scaling them to zero), saving around 50% compared to a full-time available environment. The scheduler mechanism allows the resources to be used at any desired time, bypassing the default calendar, in an easy to use way.
Application Modernisation:
Brighte had a good set of applications based on different technologies deployed across multiple AWS services. During this phase, the DNX team focused on the refactoring of the main applications to deploy the content via Docker containers and subsequently make use of ECS with spot instances.
They had previously adopted some of the 12-factor principles, but needed to improve their control over sensitive data and credentials. DNX proposed the use of AWS System Manager Parameter Store and adapted all the applications to follow this pattern.
A few serverless applications and UI static pages were deployed as part of this phase, even without demanding a strong code refactoring. We adapted the remaining apps to the 12-factor app methodology and made use of our CI/CD pipeline strategy.
Each environment in AWS was made identical, varying only in EC2 instance types in each environment (dev, uat, production). The same immutable application image was deployed and tested across these environments. By adopting this approach, Brighte has improved its operational resilience, greatly reducing production incidents to zero through its self-healing platform.
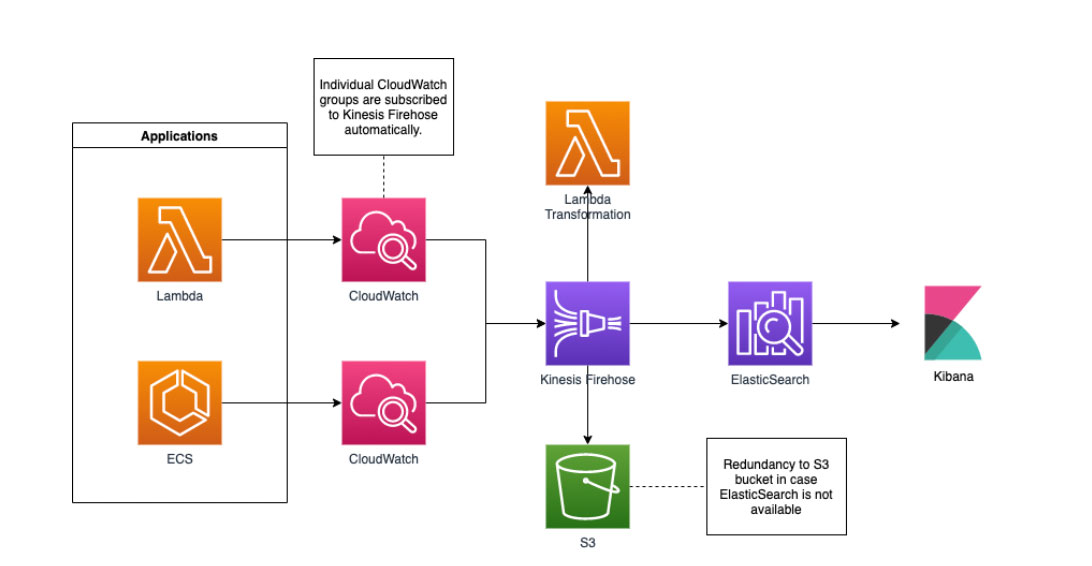
Logs:
Due to the high volume of logs, Brighte was using the ELK stack (ElasticSearch, Logstash, and Kibana) in legacy accounts to aggregate all of its application logs and avoid losing data during the process. The solution was working fine, but since it’s not a fully managed solution, the operational overhead was a point of impact.
DNX suggested the replacement of Logstash with Kinesis Firehose and CloudWatch Subscription Logs to send the data directly to ElasticSearch cluster. This way, Brighte was able to avoid the need of having dedicated resources to manage the solution and take advantage of the automatic transfer of logs between the applications, CloudWatch and ElasticSearch.
CI/CD pipeline:
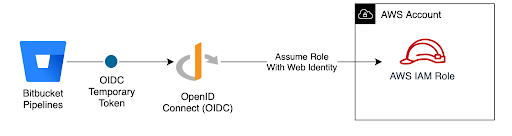
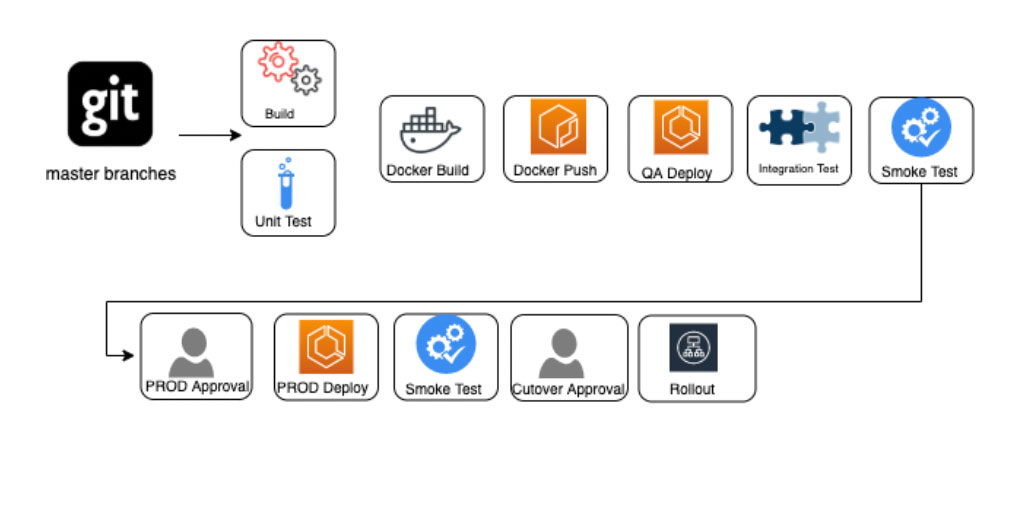
Brighte was using Bitbucket as a provider for its applications pipelines. DNX adjusted the pipeline strategy reducing the complexity of deployments across different environments and included tools to automate the replacement of data used for automated tests using AWS System Manager Parameter Store. In addition, the bitbucket pipelines have been integrated with AWS using OpenID Connect (OIDC). As a result, there is no need for creating AWS IAM users and managing AWS Keys to access AWS resources. This strategy improved security and removed any kind of sensitive data from Brighte’s codebase.
Databases:
The databases were already deployed in RDS prior to this project, but DNX increased security by encrypting all of the database workloads and improving redundancy by activating Multi-AZ strategy during the database migration phase. Also, the databases were created in dedicated and isolated subnets which allow only incoming traffic from private subnets. Therefore, the network ACLS restricts inbound traffic for specific private subnet CIDR ranges and the RDS security groups allow only inbound traffic from ECS instances.
Conclusion
From conception to its conclusion, the project was completed in approximately five months, with the restructure of AWS accounts, infrastructure resources, and a total of 15 applications migrated to the new AWS environments.
The performance of the applications is working consistently based on auto-scaling of the clusters and without any risk of downtime due to the redundancy and self-healing strategies delivered by DNX products. The infrastructure and application deployment operational overhead has reduced significantly and this is reflected directly in Brighte’s ability to release products more frequently.
With the new pattern adopted across all applications and the use of ECS clusters with spot instances, Brighte has achieved a cost reduction of 50-60% – an outstanding result for such a large set of applications and infrastructure resources used by its digital platform.
Finally, having a very secure foundation helped Brighte to provide operational cost reduction through security and best practices, as Brighte fundamentally is saving money on operating it as the complexity was going down, therefore now they are able to run faster and safer.