About Agyle Time
Agyle Time simplifies Workforce Management, ensuring cost optimisation of your resources and allowing you to better schedule to actual workload, manage costs, and improve customer satisfaction. Agyle Time uses a modern development approach with cloud technologies to engage teams and their customers with a secure and go-anywhere platform that takes just minutes to set up.
The Business Challenge
Agyle Time’s SaaS platform and its connectors are dynamic and fit different customers’ needs. However, tenant isolation along with their individual data was crucial and a mandatory requirement for large customers. In addition, due to the increase of demo requests and new tenants coming on board, building automation that delivers security was vital to keep innovating and delivering the best to Agyle Time’s users while protecting sensitive data.
Security Services on Cloud is critical for customer success in the cloud space. Data protection has become more important than ever before and every company will need high-level encryption capabilities for sensitive data, as the customers expect compliance and need governance, risk management and reporting.
DNX was engaged to elaborate and implement their new cloud operations, taking into consideration the AWS Well-Architected pillars:
- Operational Excellence
- Security
- Reliability
- Performance Efficiency
- Cost Optimisation
The Solution
Multiple perspectives should be considered while architecting automation for an SaaS arrangement like Agyle Time’s. Aspects like cross-tenant prevention, data protection, and tenant isolation are essential.
For a SaaS environment, these benefits extend beyond deployment configurations, including data encryption and security controls. This allows Agyle Time to ensure tenant isolation by encrypting their data during transit between services and in storage via their database and Amazon S3. Using Terraform also allowed Agyle Time to quickly automate their key management infrastructure, allowing employees to set up accounts for the system instantly with no third-party involvement or risk of misconfiguration.
Using Buildkite for CI/CD self-hosted pipelines, DNX has implemented automation on the CI/CD tool improving the security layer in the deployment process. For better pipeline control we decided to use self-hosted runners in our project with a custom hardware configuration which offers us better control on the builds.
It is feasible to check that secure code is deployed using CI/CD by imposing certain regulations during build time and deployment time. We’ve been able to enforce these checks with little effort because we’re utilizing Buildkite. To implement this security check, DNX used a number of plugins together with Buildkite.
The first step to an automated security architecture is to understand the kind of threats you need to protect against. Threat modelling is a technique for identifying and classifying threats that could impact your operations. It’s important to remember that any threat you document in this process is only one possible scenario out of many, but documenting it helps you better prepare yourself for how to handle it. It’s also not essential that you identify every threat, as long as you understand the general types of threats that are possible in your environment.
Going one step further, DNX has implemented a security plugin that takes care of the authentication process in Buildkite. This plugin adds some new functionalities to ensure that only authorized and authenticated users can access the CI/CD pipeline data.
The results were an automated data pipeline that brought the benefits of IaC to Agyle Time’s managed service. Each tenant’s data is isolated from the rest of Agyle Time, making it possible to enforce their multi-tenant architecture and hosting strategy using Terraform. The pipeline also allows each tenant to manage their own key infrastructure, removing any single point of failure in the account creation process.
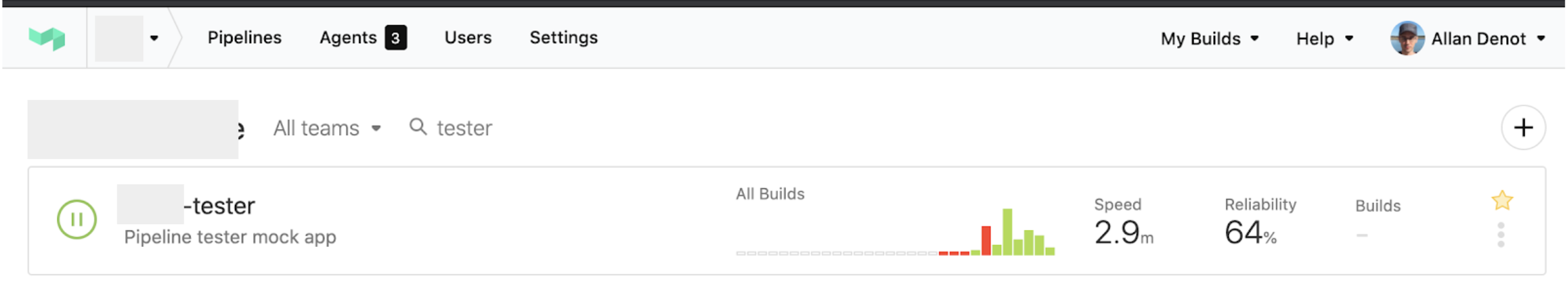
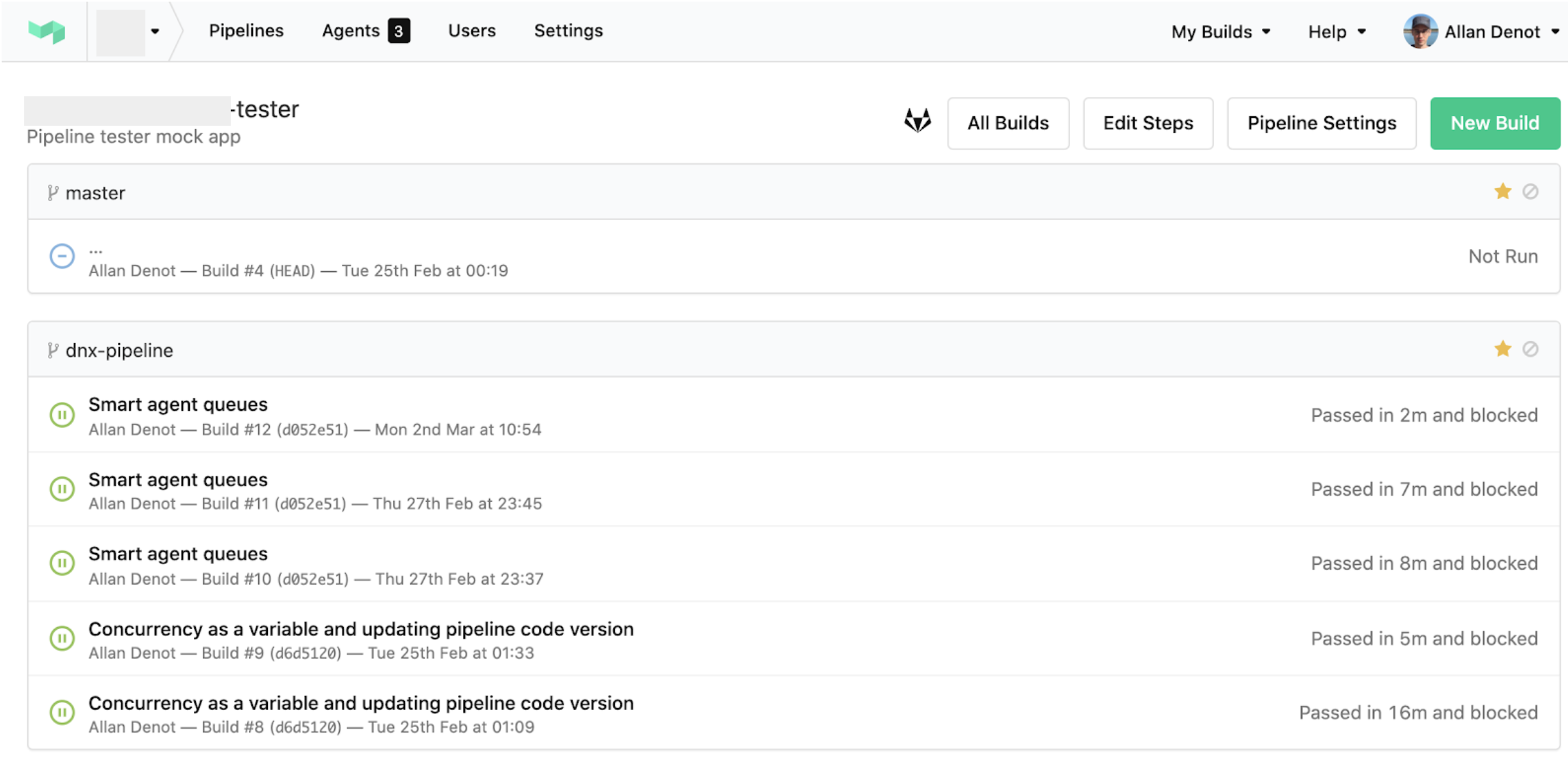
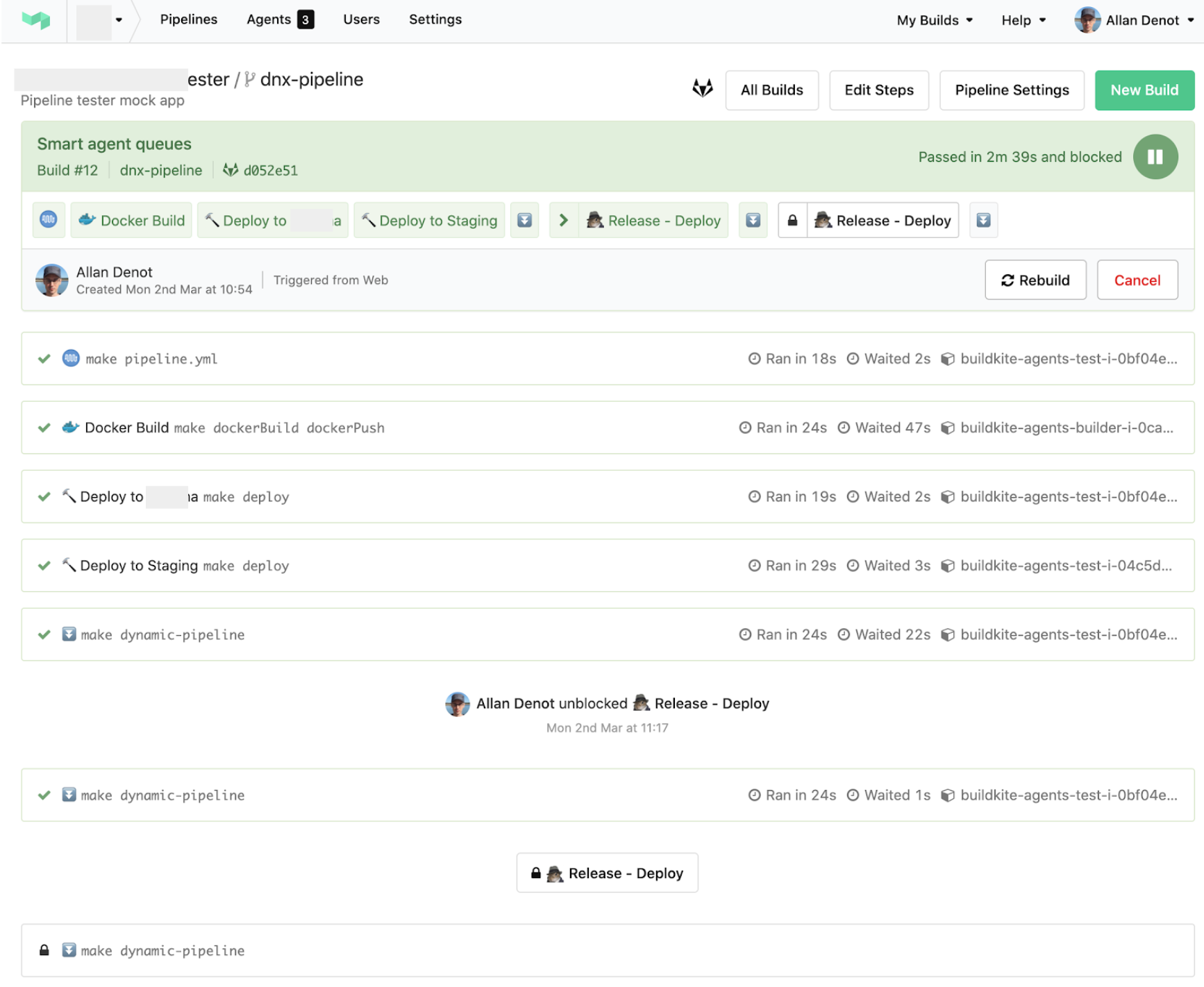
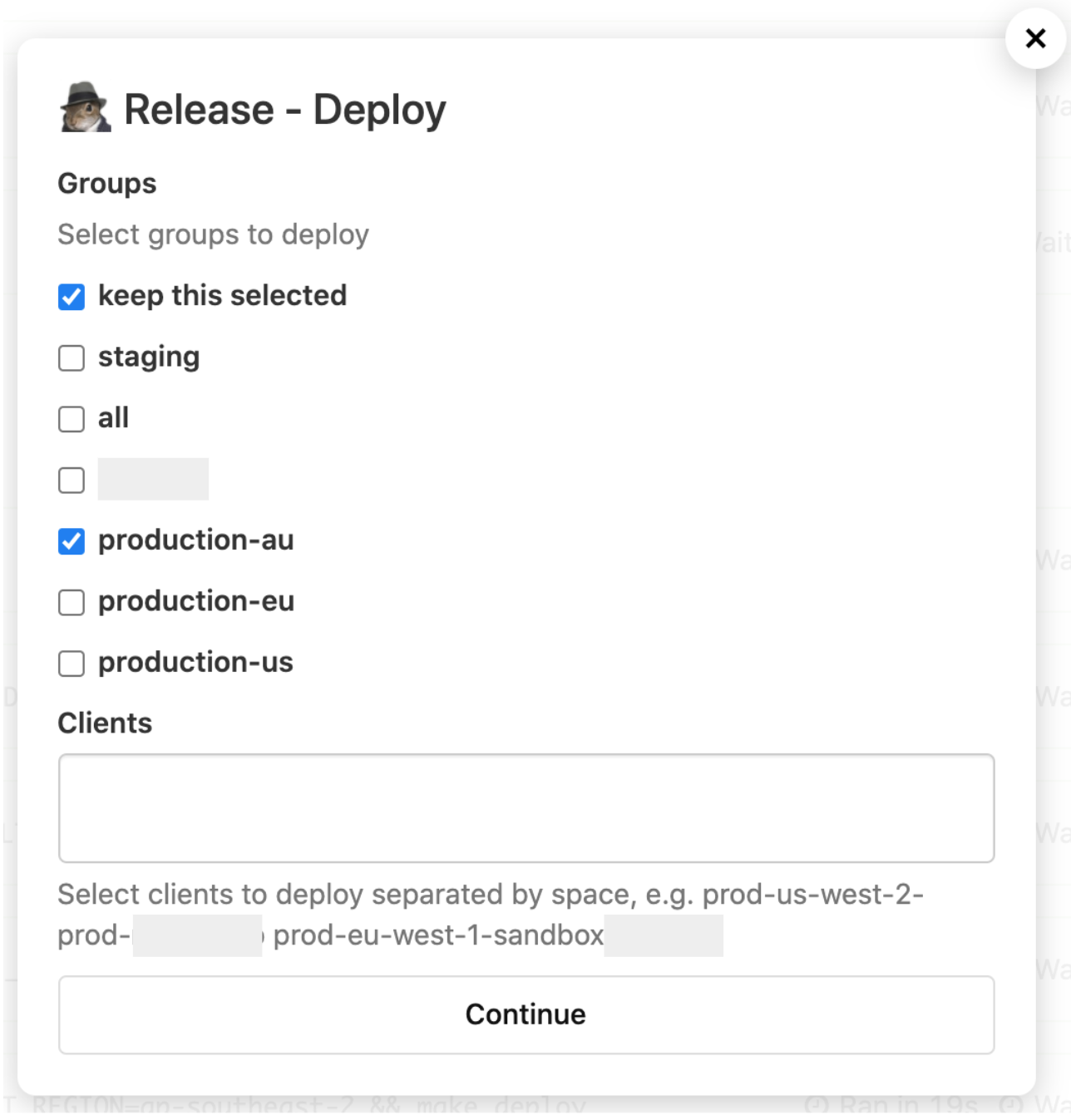
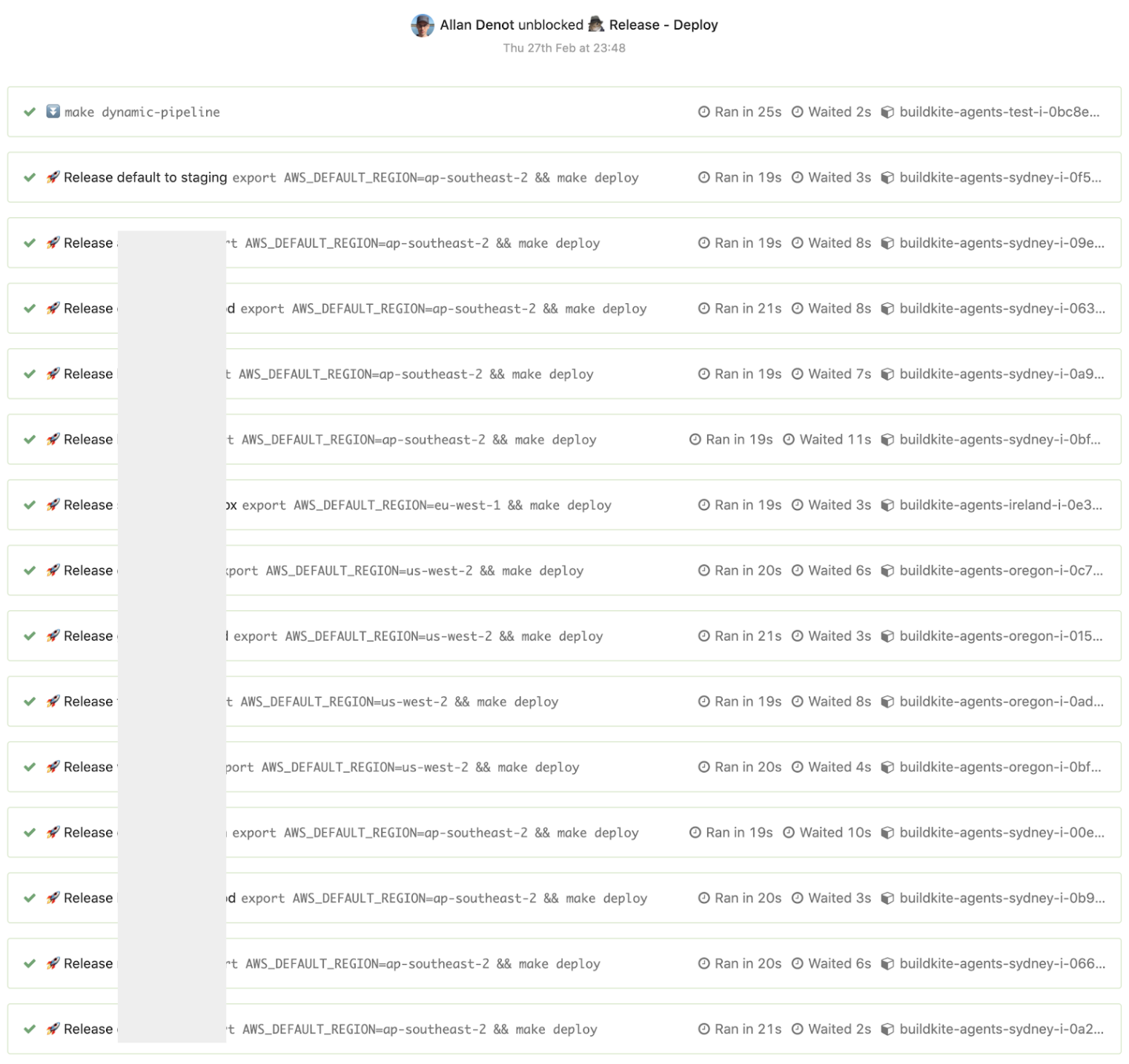
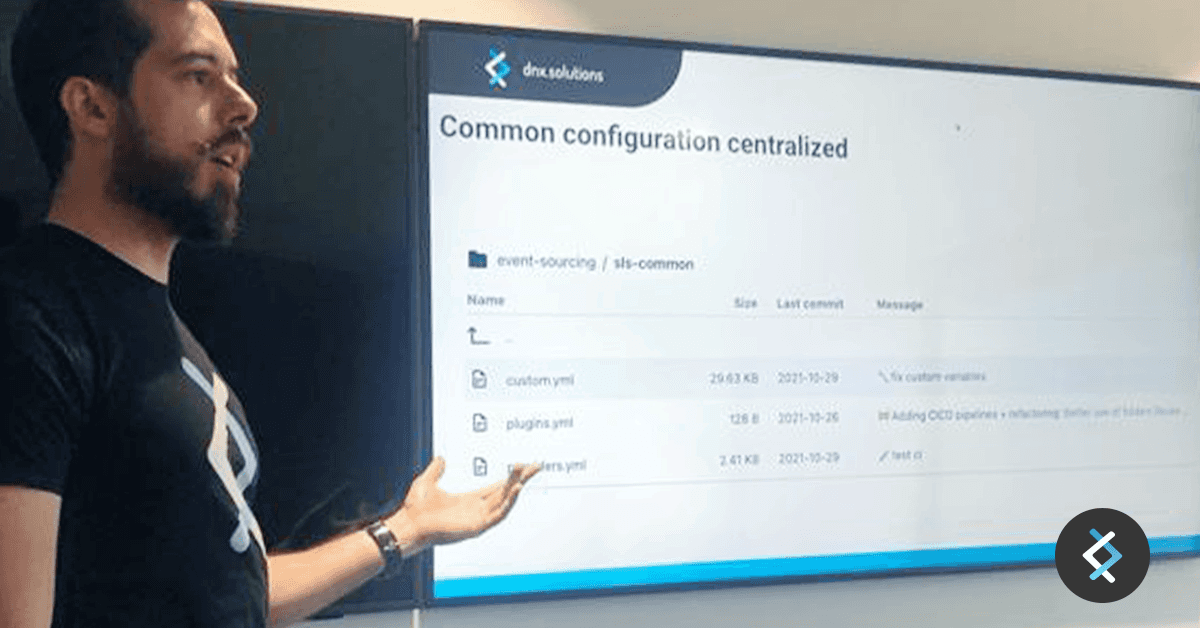
Images regarding Buildkite demo
DNX.One Foundation
We started assessing the existing Agyle Time infrastructure against the five pillars of AWS Well-Architected Framework. It enables DNX Solutions to understand customers’ environments and identify best practices gaps, then provides a remediation plan and roadmap to resolve issues based on Security, Operational Excellence, Performance Efficiency, Cost Optimisation, and Reliability.
With a thorough awareness of and recognition of infrastructure issues, DNX delivered the DNX.One Well-Architected Foundation (aka DNX.One) – an automated platform built with simplicity in mind, Infrastructure as Code (IaC), open-source technologies, and designed for AWS with well-architected principles. It means that the platform is already built based on reference architectures and continuous assurance testing to regulatory audits and analytics, removing many regulatory and compliance hurdles involved throughout an organisation’s entire lifecycle.
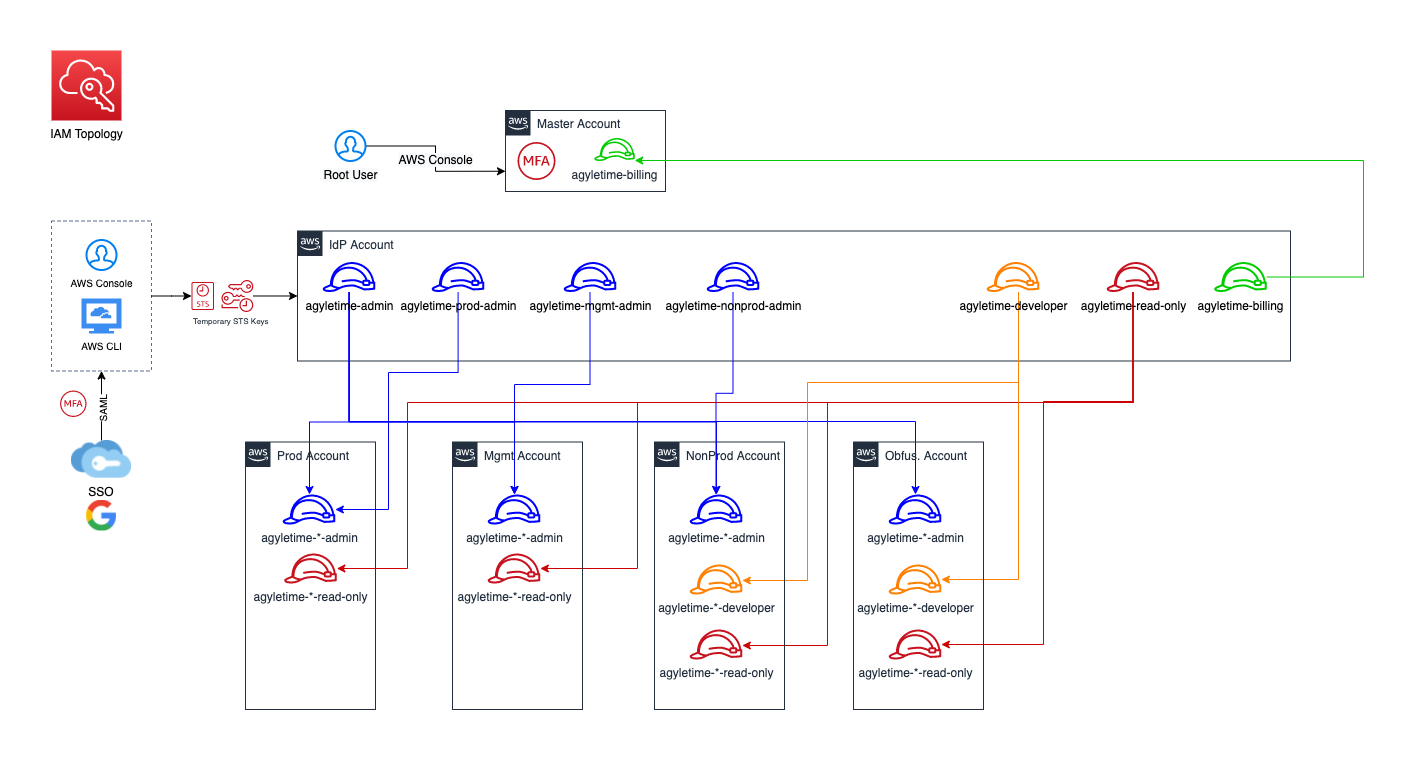
The following illustrates an example of the IAM topology implemented for Agyle Time. As AWS IAM policies are controlled and securely managed, accomplishing high standard compliance was possible. The access to AWS accounts is role-based, where users assume multiple roles across accounts and environments.
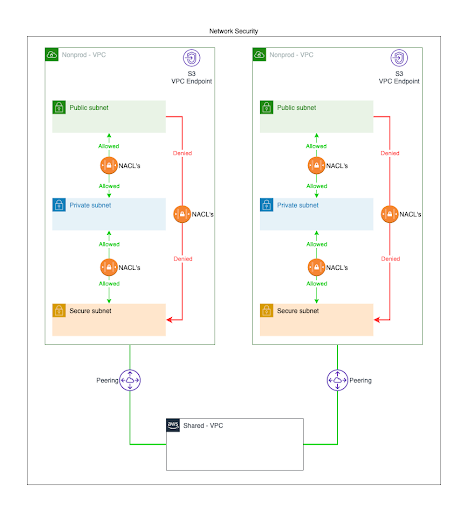
Delivery Networking using security best practices for VPC, plus the extra ‘DNX layer’ of protection, is another advantage of DNX.One. Multiple Availability Zone, security groups and network ACLs, IAM policies to control access, and tools to monitor VPC components and VPC connections are the default for DNX.One and were automatically deployed to the infrastructure. In addition, having a dedicated and isolated subnet for the database and file system was considered to enhance the security around the networking infrastructure. Therefore, there are policies, permissions, and flow access to have access to sensitive data.
Another DNX.One best practice implemented for the customer was account management and separation. This practice isolates production workloads from development, test, and shared services workloads and also provides a robust logical boundary between workloads that process data of different sensitivity levels. The granular access control determines who can access each workload and what they can do with that access. In addition, it allows the customer to set guardrails as its workloads grow.
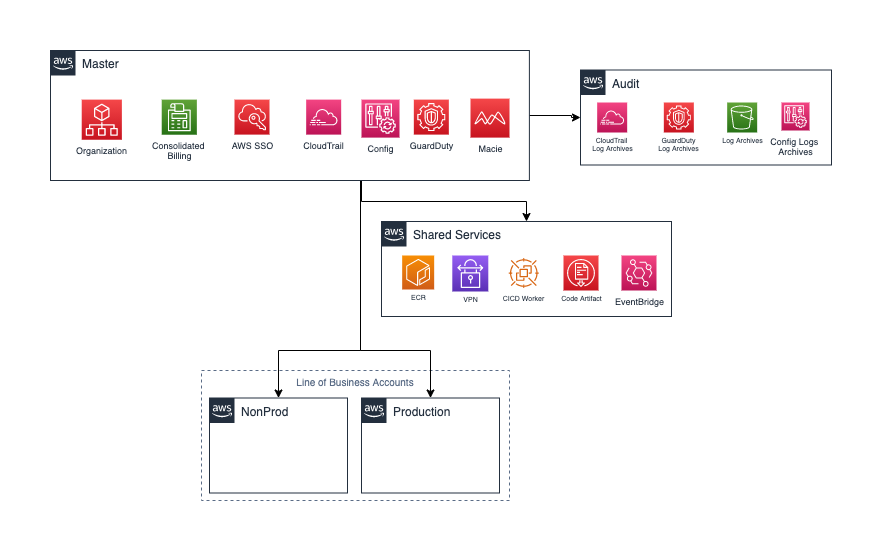
Some of the AWS Services provisioned:
Business Outcome
One of the most important topics around CI/CD pipelines is security. In public runners, provided by the pipeline tool, we cannot have control of or know if our builds are running in an isolated environment, or sharing resources across several other customers. Bringing the runners in-house, we have a stable and secure environment that enables the customer to run all the application build and deployments in isolating workspaces. Everything wrapped around the DNX.One foundation, bringing more control and confidence to the customer. Now, Agyle Time’s team can deploy releases for current and new customers automatically in a secure, elastic, and highly available way on AWS and their customers can take advantage of the workforce management platform with no data concerns.
At DNX Solutions, we work to bring a better cloud and application experience for digital-native companies in Australia. Our current focus areas are AWS, Well-Architected Solutions, Containers, ECS, Kubernetes, Continuous Integration/Continuous Delivery and Service Mesh. We are always hiring cloud engineers for our Sydney office, focusing on cloud-native concepts. Check our open-source projects at https://github.com/DNXLabs and follow us on Twitter, Linkedin or Facebook.
No spam - just releases, updates, and tech information.
Stay informed on the latest
insights and tech-updates