
Introduction to CDR Australia
Consumer Data Right (CDR) is well underway across Australia. Under the CDR framework, Data Holders (Australian banks and credit unions) will enable consented sharing of consumers’ data through standardised open Application Programming Interfaces (APIs) with Accredited Data Recipients (ADRs). By streamlining and securing the transfer of personal data, the CDR framework will completely transform the way that consumers interact with financial services in numerous sectors. With a variety of customer-centric use cases already proven in the United Kingdom and across Europe, Australian consumers now stand to benefit immensely from this next stage in the democratisation of data.
About Verifier
Verifier is the leading-edge multi-source, multi-access method solution to consumer data sharing, using the secure courier method of accessing data. This way respects the information security and privacy needs of both consumers and income data providers, while at the same time delivering ease of online processing for lenders.
Verifier has been a pioneer in consent-driven data sharing even before the rollout of CDR, providing frictionless proof of income across the Australian market using the existing data access rights within Australia’s Privacy Act (Privacy Principle 12), and has been working towards ADR status for some time. With privacy-by-design at its heart, the Regtech leader has advocated for a non-screen-scraping approach to accessing consumer data since 2014 and has actively supported the ACCC since CDR inception, becoming one of the 10 ADRs to test the framework with the four big banks. Verifier’s CEO Lisa Schutz also serves on the Consumer Data Right Advisory Committees that support standards setting in the banking and energy sectors.
The Business Challenge
To receive consumer data directly from other financial institutions through the CDR regime, an organisation must become an Accredited Data Recipient (ADR). ADRs must meet rigorous, ongoing regulatory requirements (in areas such as consent management, infrastructure, and compliance reporting) to achieve and maintain their accreditation.
When planning their participation in CDR, Verifier recognised a need for a highly automated solution that would allow the company to scale up their offerings, and constantly adapt to the evolving standards of CDR. Rather than burden their own software engineers, who were instead building Verifier’s own use cases, they turned to a community of experienced partners to help them prepare their business for becoming an ADR.
In October 2019, Verifier selected Adatree and its single API Data Recipient platform to be the CDR ‘rails’ to help them access CDR data. DNX was engaged to act as a key support for their DevOps team in tailoring a compliant CDR data environment, which is a key requirement for accreditation.
The DNX Solution
Gaining accreditation in Australia is a complex challenge, so working with experienced partners is a worthy consideration to accelerate the CDR journey. To build and deliver a compliant CDR environment, DNX (in addition to its work with Adatree) worked closely with Trend Micro Cloud One Conformity that provides tools for mapping and automating regulatory controls, and RSM as an auditor responsible for assessing compliance of what DNX delivered.
DNX.One Foundation
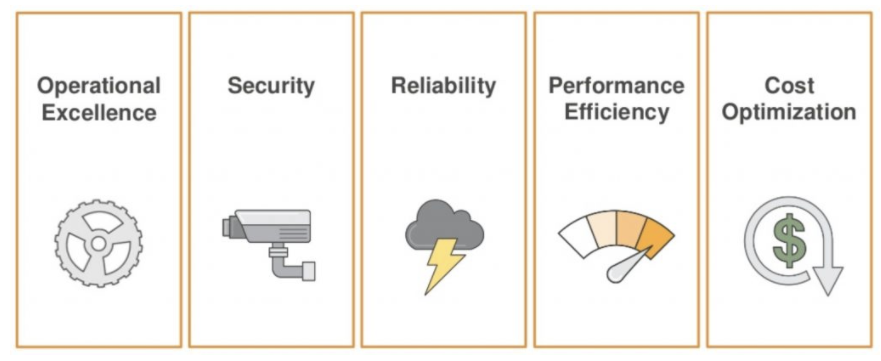
We started assessing the existing Verifier infrastructure against the five pillars of AWS Well-Architected Framework. It enables DNX to understand customers’ environment and identify best practices gaps, then provide a remediation plan and roadmap to resolve issues based on Security, Operational Excellence, Performance Efficiency, Cost Optimisation, and Reliability.
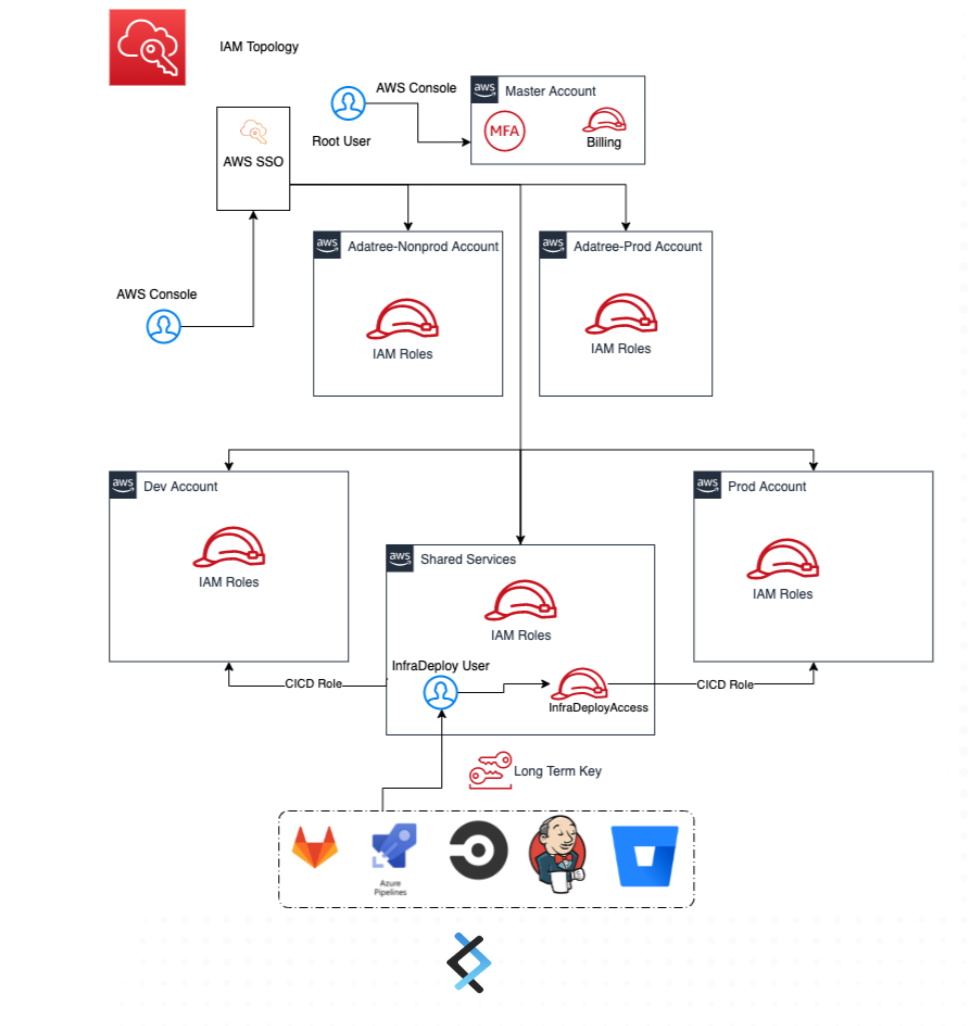
The following illustrates an example of the IAM topology that was implemented for Verifier. As AWS IAM policies are version controlled and securely managed, accomplishing high standard compliance with CDR was possible. The access to AWS accounts are role-based where users assume one or multiple roles across accounts and environments.
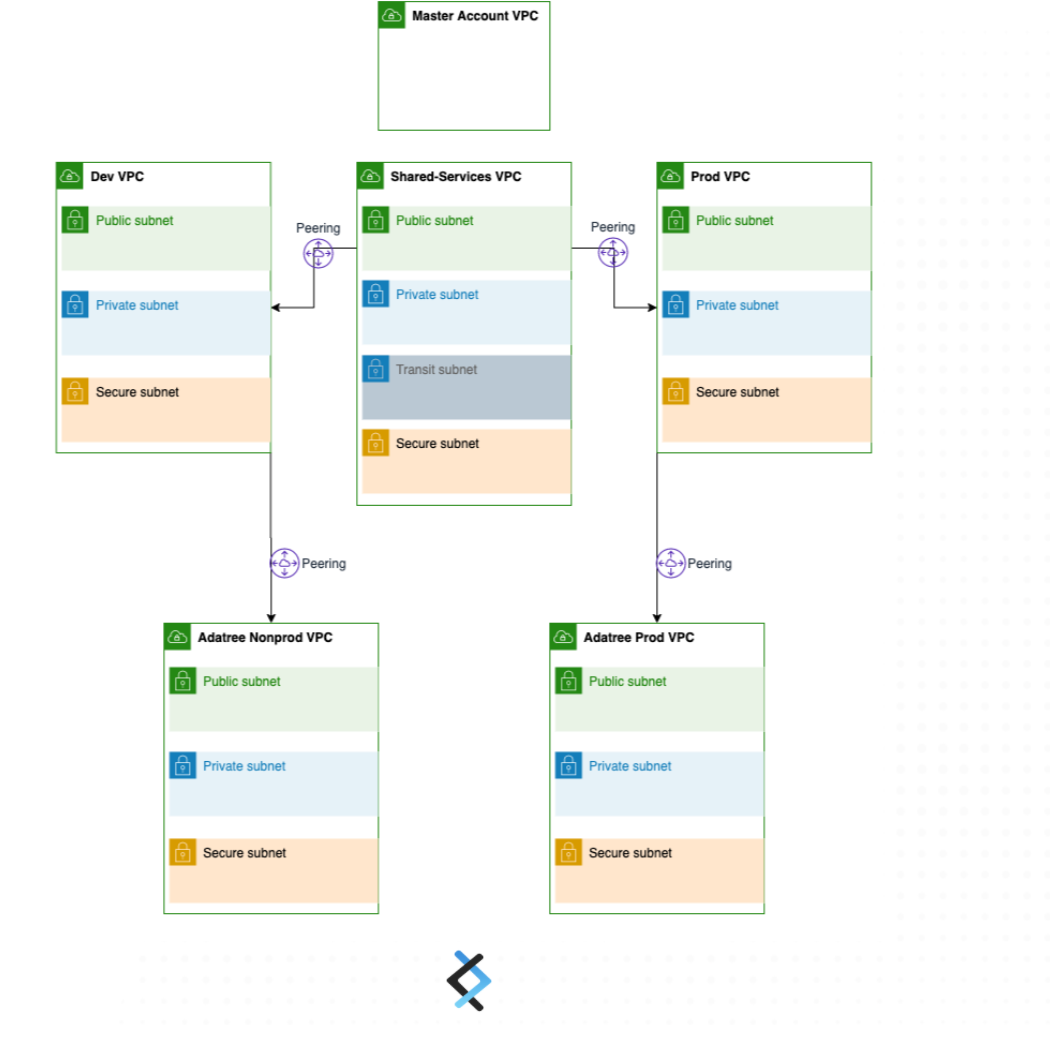
Delivery Networking using security best practices for VPC, plus the extra ‘DNX layer’ of security is another advantage of DNX.One. Multiple Availability Zone, security groups and network ACLs, IAM policies to control access, and tools to monitor VPC components and VPC connections are default for DNX.One and were automatically deployed to Verifier’s infrastructure. Having a dedicated and isolated subnet for the database and file system was considered to enhance the security around the networking infrastructure, therefore, there are policies, permissions, and flow access to have access to sensitive data.
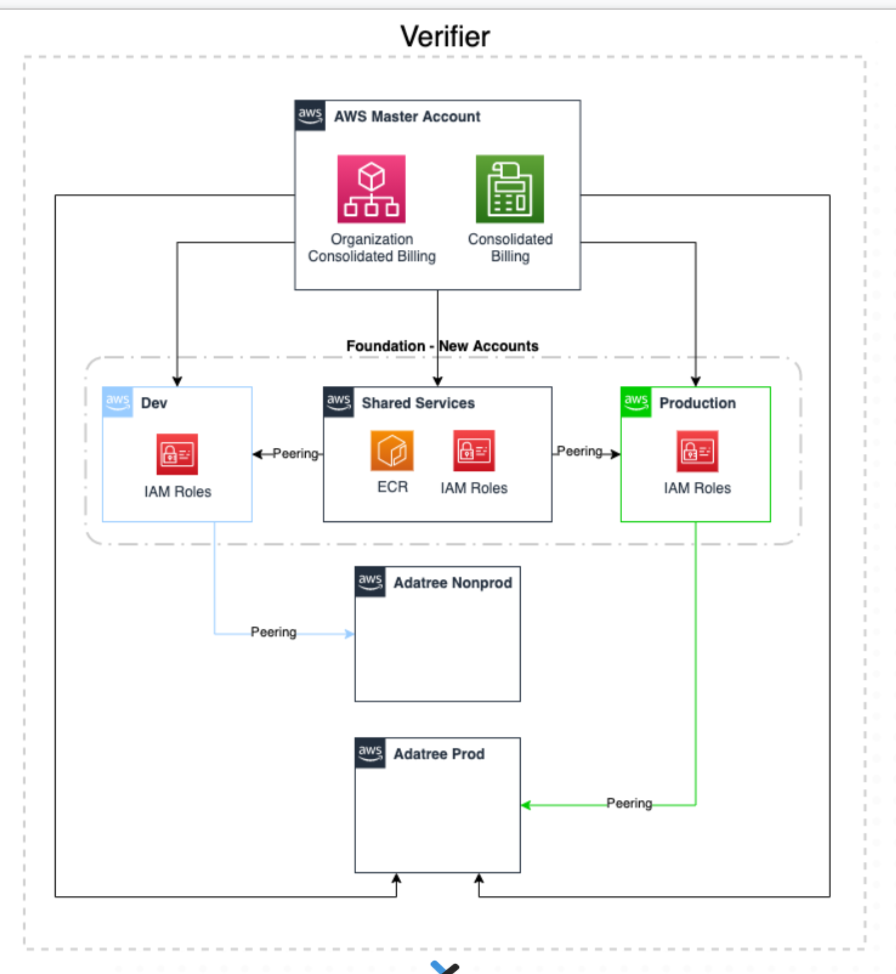
Another DNX.One best practice implemented for the Verifier environment was account management and separation. This practice isolates production workloads from development, test, and shared services workloads, and also provides a strong logical boundary between workloads that process data of different sensitivity levels, as defined by CDR requirements. The granular access control defines who can have access to each workload, as well as what they can do with that access. In addition, It allows Verifier to set guardrails as its workloads grow.
CDR Deployment + Cloud Conformity Remediation
Once we have prepared the foundation, we started deploying the CDR environment and running the Trend Micro Cloud One Conformity tool to enable automated security and compliance checks of the infrastructure. This enabled the DNX team to identify which items were not covered by DNX.One yet, focusing on building or fixing them to meet the technical security requirements requested.
It’s worthy to note that every new requirement was implemented or remediated on our DNX.One Foundation. The DNX.One Foundation has been improved and developed through ‘tried and tested’ applications, and this evolution is enabling companies to accelerate their journey to building an infrastructure compliant with the CDR.
The following are the core security aspects that DNX CDR infrastructure environment has(but not limited to):
- Networking (private networking, stateless and stateful firewalls, networking logs)
- Encryption (at rest and transit with dedicated customer keys and rotation policy)
- IAM (least privilege, SSO)
- Compute protection; and
- Incident response: anomaly detection, continuous compliance mechanisms, and alerting.
Some of the AWS Services provisioned
Conclusion
DNX achieved great outcomes working with Verifier, building a Well-Architected and Cloud Conformity AWS environment compliant with the CDR. This has effectively accelerated the audit process for Verifier by certifying that it is automatically compliant with many CDR requirements due to the DNX.One foundation already in-place, and at the same time has implemented security, reliability, operational excellence, performance efficiency, and cost optimisation using Infrastructure as Code (IaC). Cost optimisation was further enhanced with new benefits being prepared for the future. Verifier is now primed to participate in the CDR environment sooner, more dynamically, and in a more compliant manner.
At DNX Solutions, we work to bring a better cloud and application experience for digital-native companies in Australia. Our current focus areas are AWS, Well-Architected Solutions, Containers, ECS, Kubernetes, Continuous Integration/Continuous Delivery and Service Mesh. We are always hiring cloud engineers for our Sydney office, focusing on cloud-native concepts. Check our open-source projects at https://github.com/DNXLabs and follow us on Twitter, Linkedin or Facebook.



















