Today, cloud computing has become essential to many organisations’ IT infrastructure. According to Gartner, 96% of companies now use the public cloud in some way, highlighting its daily importance in the business world. While the cloud offers numerous benefits, such as flexibility, scalability, and cost-efficiency, it also brings significant security challenges. One of the most critical aspects of cloud security is protecting key identities and access credentials.
At DNX Solutions, we understand the importance of maintaining resilient cloud security measures for cloud environments. This blog post explores essential strategies and best practices for safeguarding critical identities in the cloud, focusing on root users, IAM users, and access keys. So let us take a look at some of the risks.
Understanding the Risks: Root Users, IAM Users, and Access Keys
Root User Security
The root user in AWS has unrestricted access to all resources and services in an account, making it the most powerful identity. If compromised, it could lead to catastrophic consequences.
Recommendations
- Enable Multi-Factor Authentication (MFA):
- Why: MFA adds an extra layer of security beyond just a password, requiring a second form of authentication. This is crucial for the root user, as it reduces the risk of unauthorised access.
- How: Set up MFA using hardware tokens (such as a YubiKey) and software-based solutions (like Google Authenticator). AWS allows up to 8 MFA devices to be associated with the root user. Having multiple devices ensures you have backup options in case one is lost or inaccessible.
- Block Access Key Creation:
- Why: Access keys for the root user can be highly risky if leaked or compromised.
- How: Implement Service Control Policies (SCPs) at the organisational level to prevent the creation of access keys for the root user. Access keys allow programmatic access to AWS services and should never be associated with the root account due to the risk of exposure and potential misuse. This policy enforces the best practice of disallowing the generation of access keys for the root user.
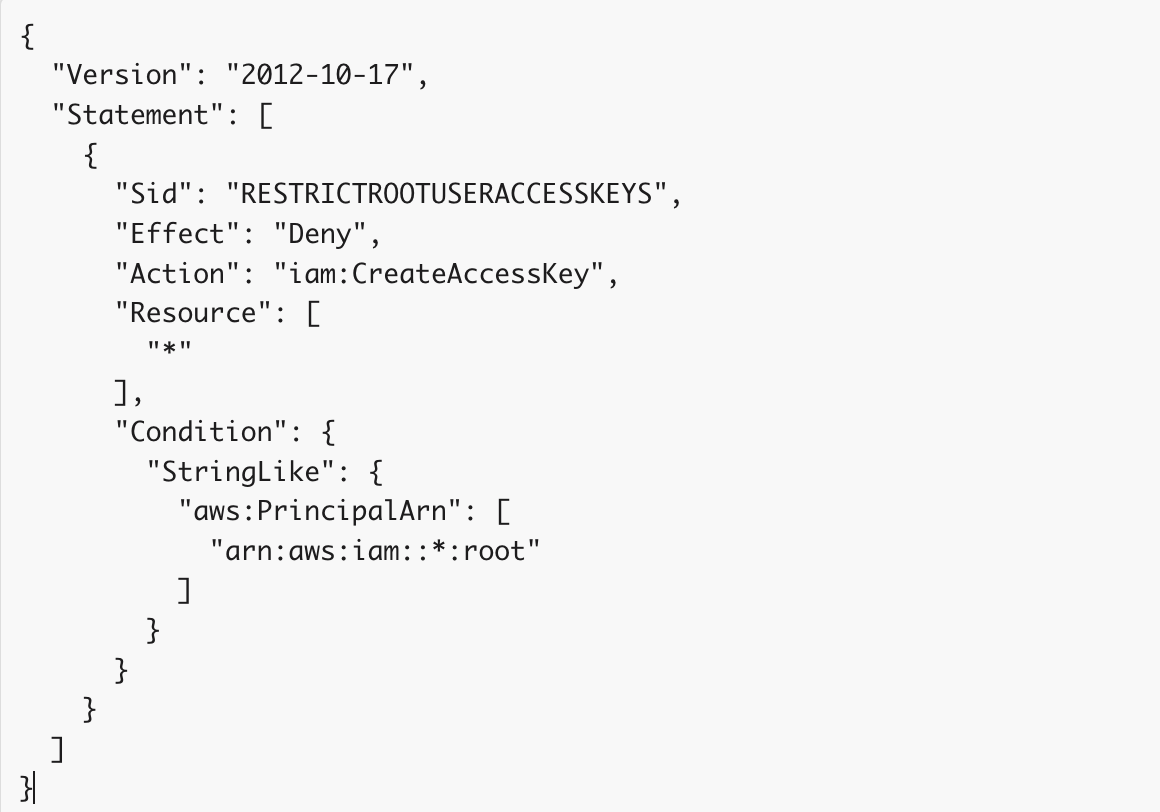
- Restrict Root User Usage:
- Why: The root user should only be used for initial account setup and specific administrative tasks that require root-level access.
Refer to the AWS guide for a detailed explanation of the specific tasks that require root user credentials - How: Use IAM roles with administrative privileges for day-to-day management instead.
Implement monitoring and alerts to notify you of any root user activity. Create a filter that detects root account usage, specify the parameters under which that usage will trigger an alarm, and provide an email address where you will receive alarm notifications.
Follow the steps provided in this AWS guide:
- Why: The root user should only be used for initial account setup and specific administrative tasks that require root-level access.
- Regular Audits and Monitoring:
- Why: Continuous monitoring helps detect unauthorised attempts to access or misuse the root user.
- How: Set up AWS Config rules and AWS Security Hub to monitor root user activity and ensure MFA is always enabled. Regularly review CloudTrail logs for any root user activity.
IAM User and Access Key Management
IAM users and access keys provide programmatic access to AWS services. If these credentials are compromised, they can be used to perform unauthorised actions.
Recommendations
- Use Least Privilege Principle:
- Why: Only grant the minimum permissions necessary for a user to perform their job.
- How: Review and update IAM policies regularly to ensure they are as restrictive as possible. Use the AWS IAM Access Analyzer to identify and mitigate overly permissive policies.
- Require MFA for All IAM Users:
- Why: Similar to the root user, requiring MFA for IAM users adds an additional security layer.
- How: Enforce MFA for all users with AWS IAM policies. Make MFA mandatory for any user with administrative or sensitive permissions
- Avoid Long-Life Credentials:
-
- Why: Credentials that do not expire pose a significant risk if compromised.
- How: Use AWS IAM roles and AWS Security Token Service (STS) to provide temporary credentials that automatically expire after a set period. Replace long-lived access keys with role-based access where possible.
- Why: Credentials that do not expire pose a significant risk if compromised.
-
- Rotate Access Keys Regularly:
- Why: Regular rotation of access keys minimises the risk associated with credential leakage.
- How: Implement a policy to rotate IAM user access keys every 90 days or less.
- Use Least Privilege Principle:
- Why: Only grant the minimum permissions necessary for a user to perform their job.
- How: Review and update IAM policies regularly to ensure they are as restrictive as possible. Use the AWS IAM Access Analyzer to identify and mitigate overly permissive policies.
- Avoid Creating IAM Users for Services (e.g., S3):
- Why: Creating IAM users with access keys for services like S3 increases the risk of key exposure and management complexity. IAM users are not the ideal solution for services leveraging IAM roles for access.
- How: Instead of creating IAM users, use IAM roles for services. For example, if an application needs to interact with S3, assign an IAM role to the EC2 instance or Lambda function running the application. This approach automatically rotates temporary credentials by AWS, reducing the risk of credential compromise and simplifying access management. This also ensures access is governed by more granular and context-aware policies attached to the roles, enhancing security and compliance.
Prioritise Single Sign-On (SSO) Over IAM Users
Relying on individual IAM users with long-lived credentials increases the risk of unauthorised access due to credential exposure, mismanagement, or inadequate controls. By using IAM users extensively, organisations face challenges in managing identities, ensuring consistent security policies, and quickly de-provisioning access when needed.
Recommendations
- Prefer Single Sign-On (SSO) Solutions:
- Why: SSO streamlines identity management by allowing users to access multiple AWS accounts and services with a single set of credentials. It reduces the need to manage individual IAM users and the associated risks of long-lived credentials.
- How: Integrate AWS IAM Identity Center (formerly AWS Single Sign-On) with your organisation’s identity provider (IdP), such as Microsoft Azure AD, Okta, or Google Workspace. This approach allows centralised management of user identities, permissions, and authentication across your AWS environment.
- Avoid Creating IAM Users:
- Why: Reducing the number of IAM users minimises the attack surface and simplifies access management. IAM users often require long-lived credentials (access keys), which can be challenging to manage and secure effectively.
- How: Instead of creating IAM users, use IAM roles that can be assumed via SSO or federated access. This ensures that users are granted temporary credentials, reducing the risk of credential compromise. Enforce this practice through organisational policies and educate teams on the benefits of using SSO.
- Implement Permission Sets via SSO:
- Why: Permission sets in AWS IAM Identity Center allow you to define fine-grained permissions for users and groups, ensuring that users only have access to the needed resources.
- How: Use permission sets to assign roles and permissions to users or groups within your IdP. This method provides a scalable and manageable way to apply the principle of least privilege across your AWS accounts, enhancing security and reducing administrative overhead.
Replace Access Methods
Instance Access Management
Traditional methods of accessing cloud instances, such as SSH for Linux servers or RDP for Windows servers, can expose your cloud environment to significant security risks. These access methods often require opening inbound ports in security groups, which can increase the attack surface of your infrastructure. Moreover, managing SSH keys or RDP credentials adds complexity and potential vulnerabilities, especially if these credentials are not rotated regularly or are exposed through misconfigurations or unauthorised access.
Adopting more secure and auditable methods of accessing instances is crucial to mitigate these risks.
Recommendations
- Disable SSH/RDP and Use AWS Systems Manager or AWS Fleet Manager
To enhance security and reduce the risks associated with traditional access methods, AWS provides alternatives such as AWS Systems Manager and AWS Fleet Manager. These services enable secure, auditable access to instances without the need for open SSH or RDP ports, significantly reducing the attack surface.- Why: AWS Systems Manager and Fleet Manager offer a more secure way to manage instances by eliminating the need for direct network connectivity via SSH or RDP, avoiding managing SSH keys or RDP credentials and reducing the likelihood of unauthorised access due to exposed or compromised credentials.
- How: Implement Session Manager or Fleet Manager, which are components of AWS Systems Manager. These allow you to connect to your EC2 instances through a secure browser-based shell or AWS CLI without needing to open inbound ports for SSH or RDP.
- .Configuration:
IAM Policies: Set up IAM policies to control access to Session Manager. This includes specifying which users can start sessions, which instances they can connect to, and what actions they can perform during those sessions.Security Groups: Review and update your security groups to remove any rules that allow SSH (port 22) or RDP (port 3389) access. This will reduce the risk of unauthorised access and limit potential attack vectors.Logging and Auditing: Enable AWS CloudTrail and AWS Systems Manager’s logging features to track all session activities. This allows for detailed auditing and monitoring of instance access, helping you detect and respond to suspicious behaviour.
- .Configuration:
Rotate Secrets Securely
Secrets Management
Insecure storage of sensitive information, such as database credentials or API keys, can result in unauthorised access and data breaches.
Recommendations
- Use AWS Secrets Manager for Storing Secrets:
- Why: Secrets Manager securely stores and manages access to secrets. It also provides automated rotation, ensuring secrets are regularly updated.
- How:Store all sensitive information, such as database credentials, in AWS Secrets Manager. Enable automatic rotation and use encryption at rest and in transit.
- Implement Regular Secret Rotation:
- Why: Regularly rotating secrets reduce the risk of them being compromised.
- How: Configure Secrets Manager to automatically rotate secrets on a schedule. Use Lambda functions to define custom rotation logic if necessary.
- Monitor and Audit Secret Usage:
- Why: Continuous monitoring helps detect unauthorised access or usage of secrets.
- How: Use CloudTrail and AWS Config to monitor access to Secrets Manager and set up alerts for suspicious activity.
Credential Rotation and Auditing
Stale or compromised credentials that are not rotated can lead to unauthorised access.
Recommendations
- Automate Credential Rotation:
- Why: Automation ensures that credentials are rotated regularly without manual intervention, reducing the risk of stale credentials.
- How: Use AWS Secrets Manager and Lambda functions to automate credential rotation. Ensure all applications are configured to handle rotated credentials seamlessly.
- Regularly Audit Access and Permissions:
- Why:Regular audits help identify over-privileged users, unused credentials, and potential security gaps.
- How:Schedule periodic audits using AWS IAM Access Analyzer, AWS Config, and AWS Security Hub to review permissions and access. Set up automated workflows to remediate issues as they are identified.
Conclusion
Securing identities in the cloud is a continuous process that requires a comprehensive approach. By following best practices such as enabling MFA, prioritising SSO over traditional IAM users, using temporary credentials, and managing secrets securely, organisations can reduce the risk of unauthorised access and credential compromise. Regular audits, automated credential rotation, and effective monitoring further strengthen security. Ultimately, cloud security is about implementing a culture of awareness and continuous improvement, ensuring that critical identities and resources are well-protected against evolving threats.
Stay Ahead of Cloud Compliance and Security Risks – Let’s Talk
As cloud technology continues to evolve, so do the risks associated with it. At DNX Solutions, we’re dedicated to helping you navigate these complexities and ensure that your cloud environment is secure and compliant. Don’t wait for a security breach to take action.
Get in touch with us today to discuss how we can assist you in fortifying your cloud security and achieving peace of mind. Our team of experts is here to provide tailored solutions that align with your needs and safeguard your critical identities.




