In the fast-changing tech world, deploying updates isn’t just about adding new features and fixing bugs—it’s about keeping cloud security strong. As we use more complex systems and handle sensitive data, there’s less room for mistakes. This blog discusses why having a solid release and deployment process is important and shares security tips to help prevent human errors and ensure updates go smoothly and safely.
Why is a Robust Process Important?
A robust release and deployment process ensures update consistency, reliability, and security. It minimises downtime, maintains data integrity, and ensures compliance with regulatory standards. Here’s why a meticulous approach is non-negotiable:
- Predictability: Structured processes make deployment outcomes predictable, reducing the chances of unexpected issues.
Quality Control: Rigorous testing and approval steps help ensure that only critically reviewed and evaluated updates are officially approved and deployed securely. - Accountability: A clear process establishes accountability by documenting who does what, which is crucial for tracing issues and managing access controls.
- Financial Stability: Preventing errors and minimising downtime through a robust process can save the company from potential financial losses, ensuring a stable and cost-effective operation.
Security Mechanisms to Prevent Human Mistakes
Human error is inevitable, but we can minimise its impact on deployments with the right tools and procedures. Git, as a version control system, plays a crucial role in this process by providing several security mechanisms and best practices:
Why Use Git? What Problems Does Git Solve?
Git manages project file versions, allows effective change tracking and collaboration, and ensures data integrity and project traceability.
- Traceability and History Management: Git provides a detailed history of project changes, making it easy to restore previous versions and enhance accountability and understanding through traceable changes.Collaboration and Parallel Development: Git supports updates from multiple contributors simultaneously, efficiently merges changes from different branches, and streamlines collaborative workflows while minimising conflicts.
- Quality Control and Stability: Git facilitates code review before merging, helps maintain a stable codebase by managing contributions, and protects against potential errors through robust version control.
Security Mechanisms and Best Practices
Here are several security mechanisms and best practices recommended to prevent human mistakes and ensure the integrity of our deployments:
- Automated Deployments: Automation reduces the need for manual intervention, decreasing the risk of human error. Tools like Github, bitbucket, GitLab, or any other CI/CD tool can automate various stages of the release process, from code commit to production deployment.
- Version Control System: Git allows us to track every change made to the codebase. Each commit is recorded with detailed information about what was changed, who made the change, and why it was made. This traceability ensures that we can always understand the evolution of the codebase and quickly identify the source of any issues.
- Code Review and Pair Programming: Implement mandatory code reviews and encourage pair programming. These practices improve code quality and ensure that at least two sets of eyes have examined the changes for potential security issues before they are merged.
- Quality Control and Stability: By managing how changes are introduced to the main branch, Git helps maintain the stability and reliability of the codebase. It allows for code reviews, automated testing, and other quality control measures before merging changes.
- Pre-deployment Checklists: Create comprehensive pre-deployment checklists that must be completed before a release goes live. These checklists should cover security checks, testing results, and deployment steps to ensure everything is noticed.
- Role-Based Access Control (RBAC): Implementing Role-Based Access Control (RBAC) with the principle of least privilege minimises the risk of unauthorised changes by restricting access to deployment tools and environments based on specific roles. This ensures that only personnel with the necessary training and clearance can push changes to production environments.
- Regular Security Training: Keep your team updated on security practices and compliance requirements. Regular training sessions can dramatically reduce the risk of human error by keeping security at the forefront of your team’s mind.
- Post-Deployment Monitoring: Implement monitoring tools to detect and respond to issues quickly. Monitoring can also help you understand the impact of the deployment and rolling back changes if necessary.
- Clear Rollback Process: Establish a clear rollback process to ensure the recovery from deployment issues. This includes:
- Preparation and Planning: Ensure regular backups and document a rollback plan.
- Triggering a Rollback: Define criteria for rollback and decision-making roles.
- Rollback Execution: Use automated scripts to revert code and databases, followed by thorough testing.
- Post-Rollback: Perform root cause analysis, document the incident, and improve processes based on lessons learned.
Protect Your Main Branch: Ensuring Integrity and Stability
Protecting our main branch is essential for maintaining the integrity and reliability of our project’s codebase. The main branch is often the main or default branch in a repository, representing the most up-to-date and stable project version. Actions that can be taken to ensure stability, quality control, security, and consistency include:
- Block Updates to Main Branch: Direct updates to the main branch can lead to several issues: unstable builds, accidental deployment of unreviewed code, and potential security vulnerabilities. Many teams implement a policy to mitigate these risks where direct commits to the main branch are disabled. Instead, all changes must go through a separate development branch or branches and merge into main after sufficient review. Here is how this process generally works:
- Branching: Developers create feature branches from the main branch to work on specific tasks or features
- Code Commit: Changes are committed to these feature branches, not directly to the main.
- Pull Request: Once a feature is complete, developers open a pull request to merge the changes back into the main branch.
This flow not only keeps the main branch stable but also ensures that every change is accounted for and can be traced back to a specific branch and purpose.
- Enhance Security with Blocked Updates and Mandatory Approvals: When it comes to managing deployments, particularly in critical or large-scale environments, controlling how changes are introduced to the main branch is essential. The main branch, often considered the “source of truth” in many development workflows, should always reflect a stable and reliable state.
- Wait for Approval: Before any code is merged into the main, it should be reviewed and approved by designated team members. This review process serves multiple purposes:
-
Static code analysis: Reviewers check the code for quality, adherence to coding standards, and alignment with the project’s architecture and design principles.
- Example of tools: SonarQube, CodeClimate (for Github users), Synk and Codacy.
- Suggestions:
- Configure your tools according to your project’s coding standards and security requirements
- Review and refine your static analysis rules regularly to adapt to new coding practices and avoid unnecessary noise in the reports.
-
Security Scanning: Code is scanned for potential security issues. Many teams use automated tools to detect vulnerabilities that could be exploited by attackers.
- Example of tools: OWASP ZAP, Fortify, Wiz and SnykC
- Suggestions:
- Security tools should be configured to run at least daily or triggered by significant changes in the codebase.
- Regularly update the vulnerability databases and adjust the scanning profiles to cover new and emerging threats.
- Prioritise and fix the vulnerabilities based on their severity and the potential impact on the application.
-
Performance Impact: Reviewers assess the potential impact of the changes on the system’s performance, ensuring that new features do not degrade the user experience or system stability
- Example of tools: New Relic,Gatling, LoadRunner, Dynatrace
- Suggestions:
- Integrate performance testing tools into your deployment cycle to test significant changes before they hit production.
- Use these tools not only to detect degradation but also to forecast how scaling up or modifying infrastructure impacts performance.
- Regular benchmarking against historical performance data can help detect performance trends and preemptively address issues.
-
Tooling and Integration
Implementing a block on direct master updates and enforcing a review process requires the right tools and integration:
- Version Control Systems: Platforms like GitHub, GitLab, and Bitbucket offer built-in support for branch protection rules, pull requests, and review processes.
- Continuous Integration (CI): Tools like Jenkins, test steps on Github, Bitbucket and CircleCI can be configured to automatically test the code before they are merged, ensuring that only code that passes all tests can be merged.
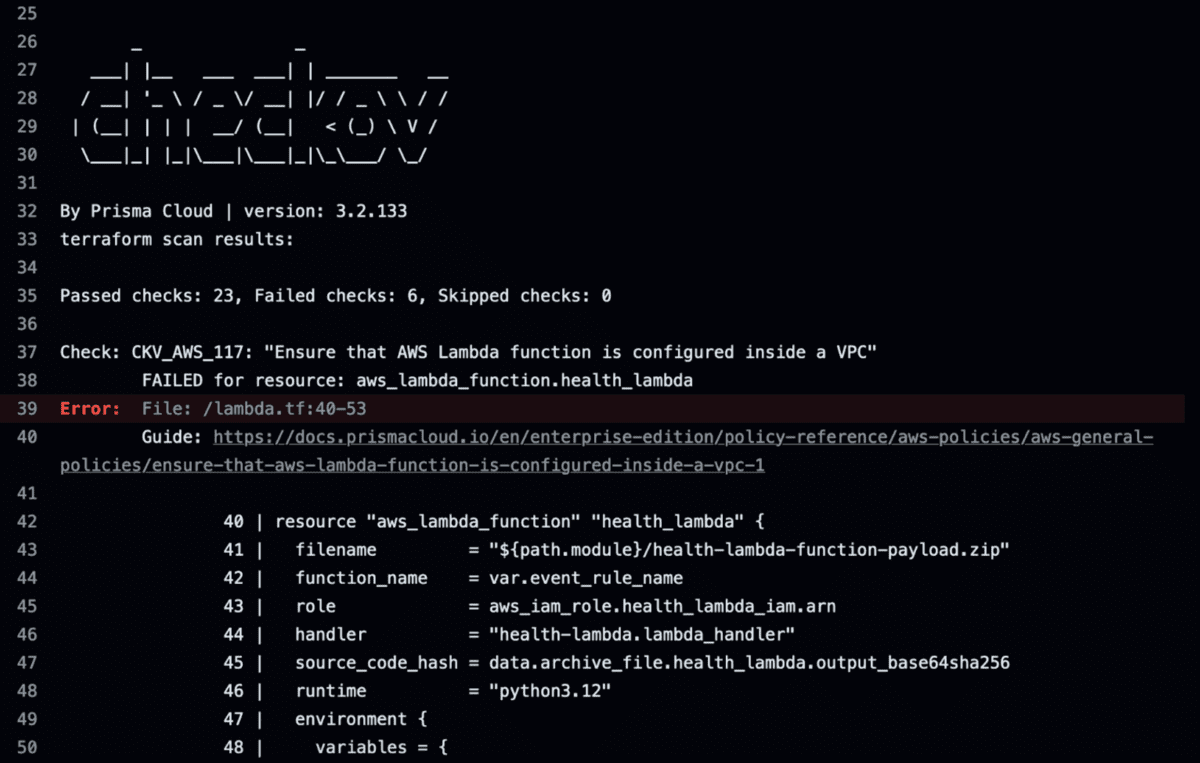
- Automated Security Tools: Integrating tools like SonarQube, Snyk, Checkov, and WIZ can automatically scan for vulnerabilities as part of the CI pipeline.
Final Words
Ready to enhance the security and efficiency of your release and deployment processes? Implement structured processes, robust security mechanisms, and rigorous quality controls to safeguard your systems. Start today and reach out to us to learn how we can help you achieve these goals.
Enhance Security and Efficiency in Your Release and Deployment Processes Today
Challenge the status quo, break free from old paradigms, and explore the vast potential of AWS. Get in touch with us today to request your free assessment and start your journey toward transformative growth.


























